Difference between revisions of "Security setup"
| (6 intermediate revisions by the same user not shown) | |||
| Line 3: | Line 3: | ||
[[File:Security_1.PNG|center]] | [[File:Security_1.PNG|center|link=]] | ||
The setups that you can made to enhance the security of Tactic is presented below: | The setups that you can made to enhance the security of Tactic is presented below: | ||
* You can add a CAPTCHA on the log-in page as well as some advanced permissions and session out time. | * You can add a CAPTCHA on the log-in page as well as some advanced permissions and session out time. | ||
[[File:Security_2.PNG|center|link=]] | |||
* You can add password security | * You can add password security | ||
* External and internet access security | * External and internet access security | ||
| Line 27: | Line 33: | ||
[[File:Security_3.PNG|center]] | [[File:Security_3.PNG|center|link=]] | ||
== Parameters == | == Parameters == | ||
| Line 39: | Line 45: | ||
* Connection timeout in seconds and | * Connection timeout in seconds and | ||
* Response timeout in seconds | * Response timeout in seconds | ||
== Proxy == | == Proxy == | ||
This proxy setup allows you to let Tactic access internet through a proxy server in the time of need. You need to remember that this is not directly associated with your browser settings, activating this settings only allow Tactic to access internet from uncommon resources for a time being. For confirming Tactic to use the proxy settings you need to allow the field of “Use a proxy server (otherwise access is direct to the internet)” by clicking on “Yes”. After clicking on Yes, you need to fill up the four fields that will be shown on the same page. The fields are presented below: | This proxy setup allows you to let Tactic access internet through a proxy server in the time of need. You need to remember that this is not directly associated with your browser settings, activating this settings only allow Tactic to access internet from uncommon resources for a time being. For confirming Tactic to use the proxy settings you need to allow the field of “Use a proxy server (otherwise access is direct to the internet)” by clicking on “Yes”. After clicking on Yes, you need to fill up the four fields that will be shown on the same page. The fields are presented below: | ||
* Proxy server: Name/Address | * '''Proxy server''': Name/Address | ||
* Proxy server: Port | * '''Proxy server''': Port | ||
* Proxy server: Login/User | * '''Proxy server''': Login/User | ||
* Proxy server: Password | * '''Proxy server''': Password | ||
[[File:Security_4.PNG|center|link=]] | |||
== Audit == | == Audit == | ||
With the help of this setup, you can activate Audit trail. You can find out the details from '''Admin tools -> Audit'''. | With the help of this setup, you can activate Audit trail. You can find out the details from '''Admin tools -> Audit'''. | ||
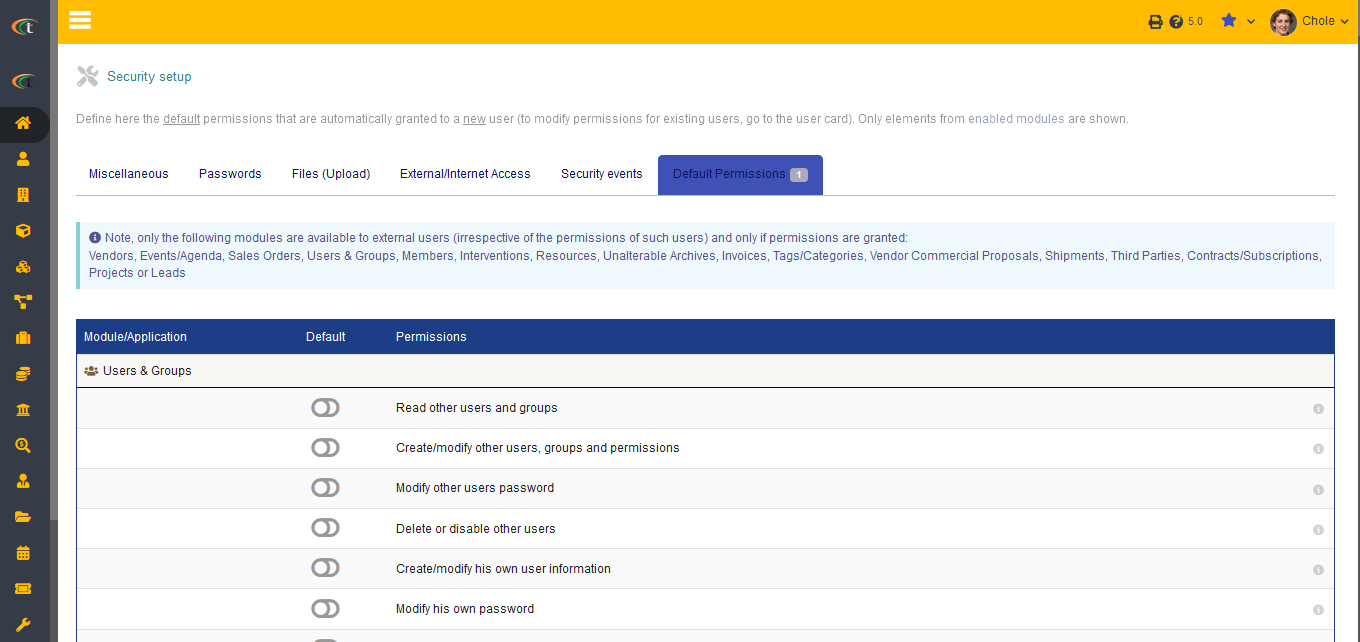
= Default permissions = | = Default permissions = | ||
Default permissions are the access that are given to the new users upon creation. It is the same for every new user that is created in Tactic. However, these default permissions do not impact the existing permissions in any way. The admins are by default provided with the read, edit and delete access of all the external and internal module. Moreover, there can be some modules, which have more access than others to be defined. Hence, the admins can change access by clicking on the plus (+) sign to add or by clicking on the minus (-) sign to remove. | Default permissions are the access that are given to the new users upon creation. It is the same for every new user that is created in Tactic. However, these default permissions do not impact the existing permissions in any way. The admins are by default provided with the read, edit and delete access of all the external and internal module. Moreover, there can be some modules, which have more access than others to be defined. Hence, the admins can change access by clicking on the plus '''(+)''' sign to add or by clicking on the minus '''(-)''' sign to remove. | ||
Tactic recommends you to be very careful while handling this settings. As this settings allow you to set default rules for all the new users, they can easily be granted to see or do anything in Tactic if you provide them with unnecessary access in Tactic. You can set this with more accuracy by going to User->right screen. You can also create security group and include the users. | |||
Tactic recommends you to be very careful while handling this settings. As this settings allow you to set default rules for all the new users, they can easily be granted to see or do anything in Tactic if you provide them with unnecessary access in Tactic. You can set this with more accuracy by going to '''User->right screen'''. You can also create security group and include the users. | |||
[[File:Security_6.PNG|center|link=]] | |||
Latest revision as of 10:42, 1 July 2022
Introduction
Setting up the security infrastructure for Tactic is a crucial task that needs to be completed without having any loopholes. Tactic provides you with the facility of setting up a number of behaviour that is associated with Tactic’s technical and functional assets, you can access the same by going to the path of Home-> setup-> Security.
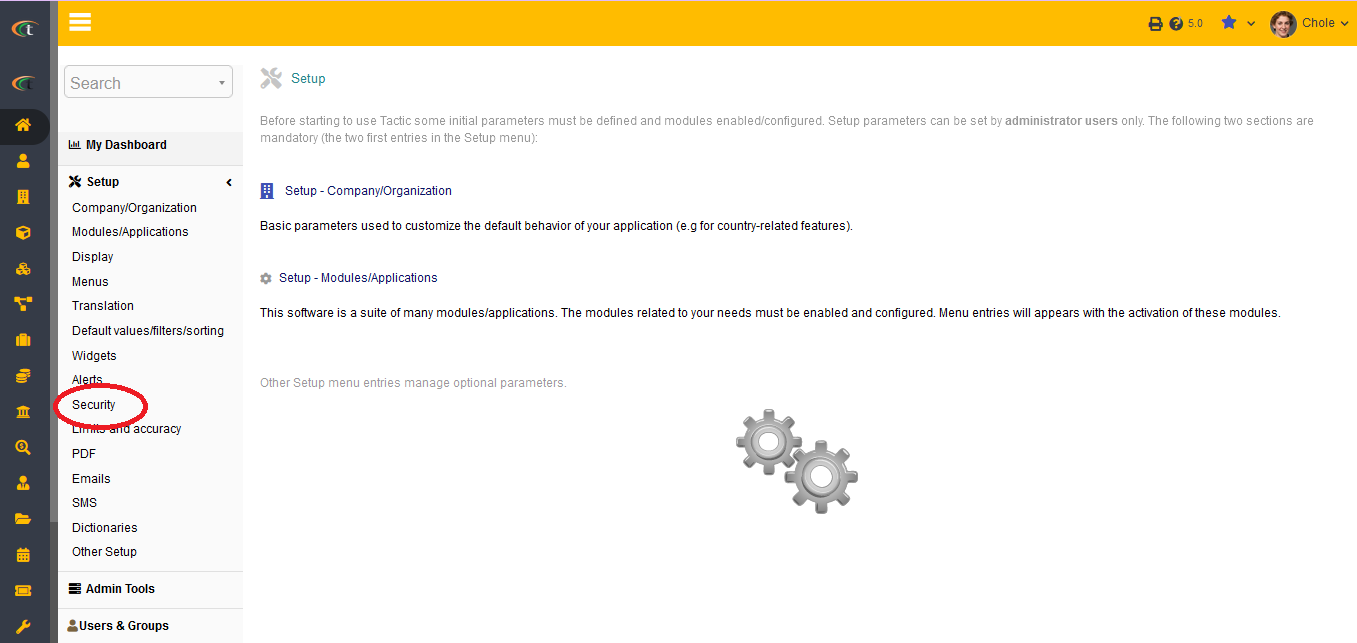
The setups that you can made to enhance the security of Tactic is presented below:
- You can add a CAPTCHA on the log-in page as well as some advanced permissions and session out time.
- You can add password security
- External and internet access security
- Audit
- Permissions that are provided by default
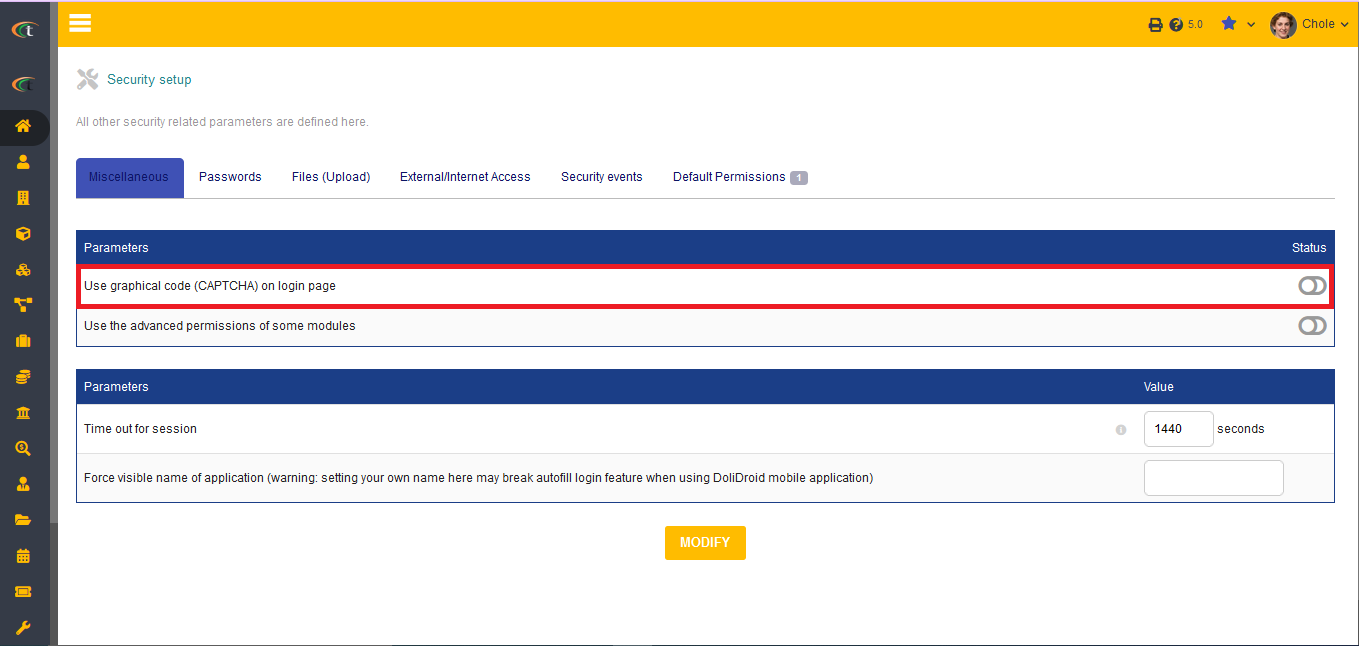
Miscellaneous
On the miscellaneous tab you get a number of features to setup. The features are presented below:
- You can set up the usage of graphical code on the log-in page. If the users activate it then a CAPTCHA will be required each time a user try to login to Tactic. For activating it the users only need to click the option of Yes in the setup page.
- You can use advanced permission for some modules to enhance the security of the SaaS even more. For activating it the users only need to click the option of Yes in the setup page.
- Session time out settings ensures to delete users’ sessions after a specific time being.
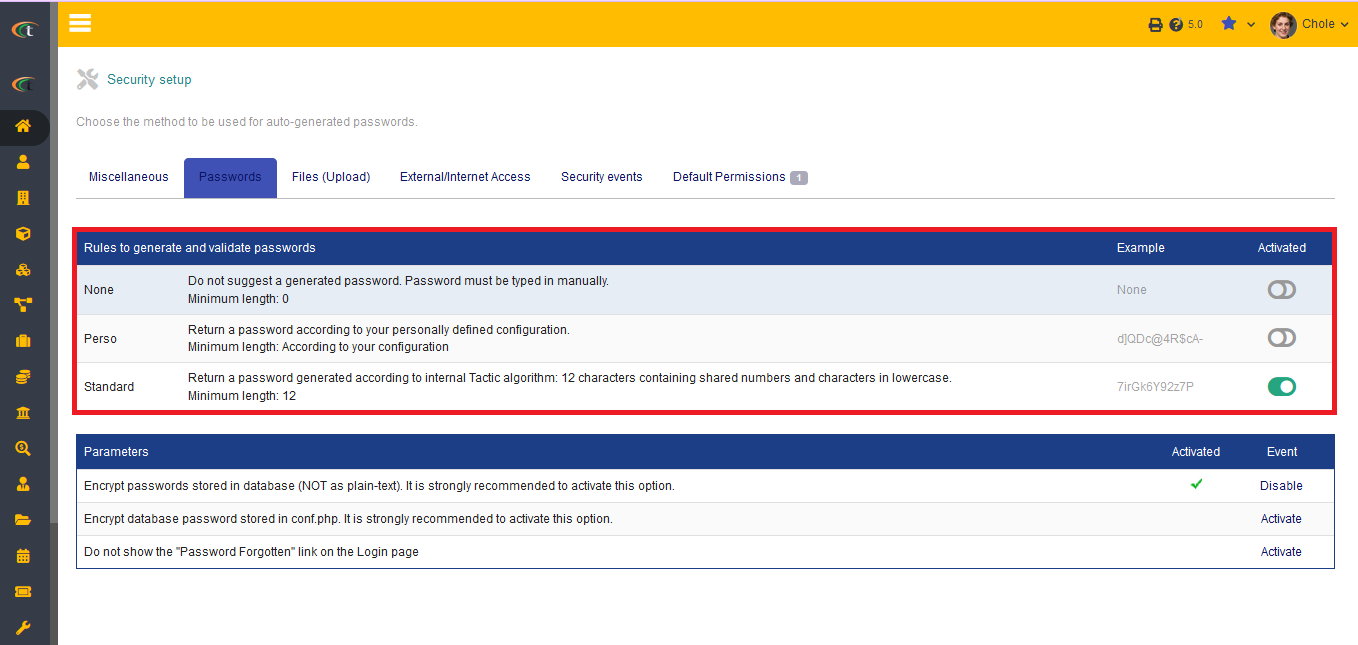
Passwords
Generation and validation of passwords
There are three implemented rules that can be used for password generation and validation. You can use one of these three rules, the rules are presented below:
- Perso: With the help of this rule you can define and establish your own password rule, which need to be followed by the users.
- None: Users can setup password as they like there is no rule at all. However, this setup is not recommended at all.
- Standard: The standard option urges you to use 8 characters containing numbers and lowercase alphabets.
You can choose any of the rules and click on the option of "Activate" to start using it.
Parameters
Three additional parameters are provided with Tactic. It is recommended to activate the parameters for better experience and security.
- Encryption of passwords that are stored in database.
- Encryption of database password stored in conf.php.
- Not showing the "Password Forgotten" link on the login page.
External/internet access
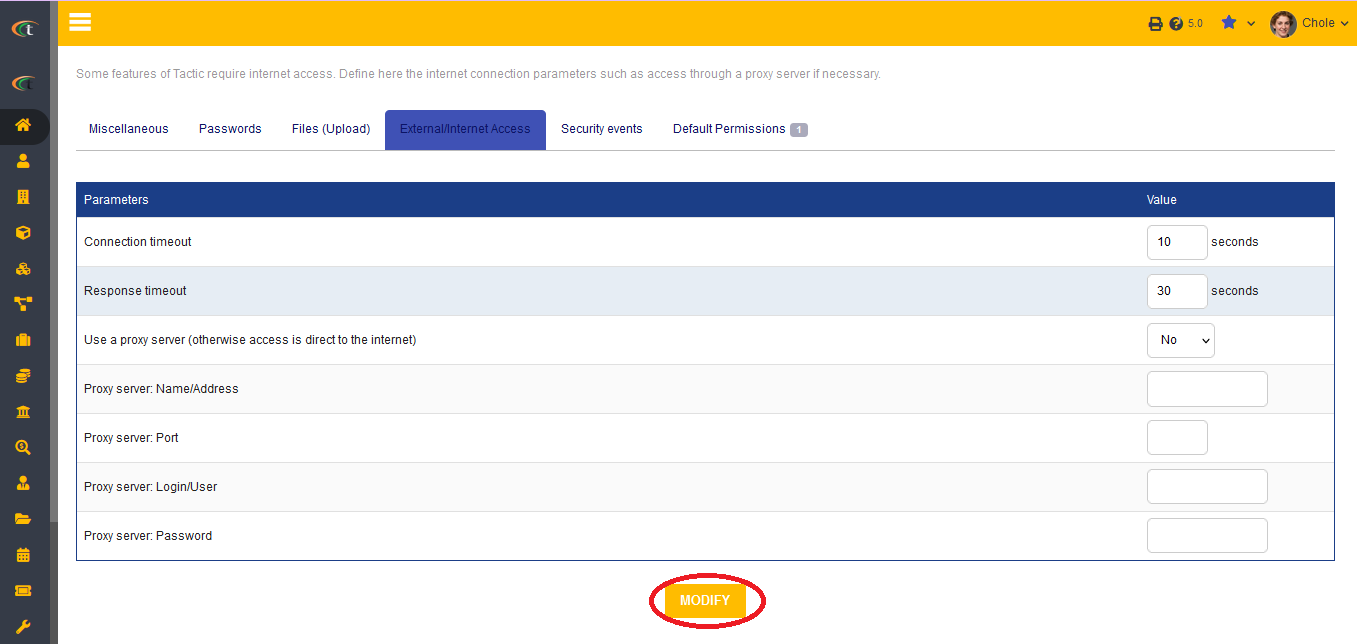
Timeout
For external sites two types of timeouts can be set, which are:
- Connection timeout in seconds and
- Response timeout in seconds
Proxy
This proxy setup allows you to let Tactic access internet through a proxy server in the time of need. You need to remember that this is not directly associated with your browser settings, activating this settings only allow Tactic to access internet from uncommon resources for a time being. For confirming Tactic to use the proxy settings you need to allow the field of “Use a proxy server (otherwise access is direct to the internet)” by clicking on “Yes”. After clicking on Yes, you need to fill up the four fields that will be shown on the same page. The fields are presented below:
- Proxy server: Name/Address
- Proxy server: Port
- Proxy server: Login/User
- Proxy server: Password
Audit
With the help of this setup, you can activate Audit trail. You can find out the details from Admin tools -> Audit.
Default permissions
Default permissions are the access that are given to the new users upon creation. It is the same for every new user that is created in Tactic. However, these default permissions do not impact the existing permissions in any way. The admins are by default provided with the read, edit and delete access of all the external and internal module. Moreover, there can be some modules, which have more access than others to be defined. Hence, the admins can change access by clicking on the plus (+) sign to add or by clicking on the minus (-) sign to remove.
Tactic recommends you to be very careful while handling this settings. As this settings allow you to set default rules for all the new users, they can easily be granted to see or do anything in Tactic if you provide them with unnecessary access in Tactic. You can set this with more accuracy by going to User->right screen. You can also create security group and include the users.